Last updated:
 Why Trust Cryptonews
Why Trust Cryptonews

Ledger has released a detailed security report analyzing the latest Trezor Safe 3 and Safe 5 hardware wallets, highlighting significant security improvements over previous Trezor models.
However, despite these advancements, Ledger warns that the new devices remain vulnerable to specific supply chain attacks due to their reliance on a microcontroller for cryptographic operations.
Ledger’s Security Analysis of Trezor Safe Devices
Since its inception, Ledger Donjon has actively conducted open security research on various hardware wallets, including previous Trezor models, such as the Trezor One and Trezor T.
These earlier devices were found to be highly susceptible to physical seed recovery attacks due to their dependence on standard microcontrollers, which are not designed to withstand hardware-based attacks such as voltage glitching.
The release of the Trezor Safe 3 in late 2023, followed by the Safe 5 in mid-2024, marked a major security upgrade for Trezor.
Unlike their predecessors, the new models incorporate an EAL6+-certified Secure Element alongside a microcontroller.
According to Charles Guillemet, CTO Ledger, the Secure Element now handles PIN verification and key storage, making it harder for attackers to extract a user’s private keys through conventional means.
Despite these improvements, Ledger’s research found that the devices still have potential weaknesses.
Specifically, all cryptographic operations, such as transaction signing, are still performed on a microcontroller that remains vulnerable to firmware manipulation.
If an attacker gains access to a device during manufacturing or transit (a supply chain attack), they could modify the software running on the microcontroller, compromising the device before it even reaches the user.
Ledger’s report elaborates on the implications of these findings, making it clear that this kind of attack could lead to the complete remote theft of a user’s funds without their knowledge, even if they believe their hardware wallet is secure.
Supply Chain Attack Risks and Implications
A key focus of Ledger’s research is the risk posed by supply chain attacks. A fundamental issue with the Trezor Safe 3 and Safe 5 models is their method of firmware integrity verification.
The Secure Element inside these devices ensures that PIN protection remains robust, but it does not attest to the authenticity of the firmware running on the microcontroller.
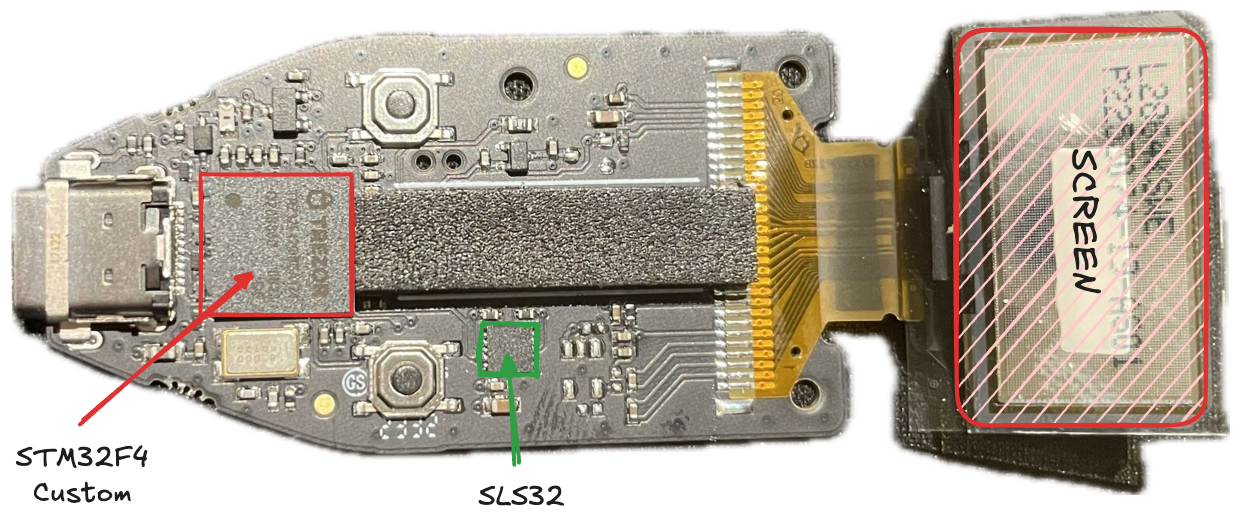
Ledger’s analysis found that the microcontroller used in Trezor Safe devices, labeled TRZ32F429 (a customized STM32F429 chip), is vulnerable to voltage glitching attacks.
This allows a sophisticated attacker to read and modify the firmware stored in the device’s flash memory.
Since Trezor relies on a pre-shared secret between the Secure Element and the microcontroller for authenticity verification, an attacker could extract this secret via a glitching attack and reprogram the device while appearing genuine to the user.
This means that if an attacker infiltrates the supply chain during production or distribution, they could implant malicious firmware that appears to function normally but secretly exposes user keys or modifies transaction details.
Unlike direct physical attacks, which require an adversary to have the wallet in hand, a supply chain attack could allow the large-scale compromise of devices before they even reach customers.
Trezor Assures Funds Safety
Following Ledger’s report, users have been inquiring if their funds are safe and if this discovery won’t affect their security.
Responding to a similar user request on X, the Trezor team commented that funds are safe and the discovered exploit is a previously known attack.
However, some question why it hasn’t been patched since it is known. This latest discovery comes particularly after a report from January 2024 showed that a security breach exposed the contact information of nearly 66,000 Trezor users.
As of now, the Trezor team has not made any official comment on the report, but Trezor users are eager to hear what the team has to say or how a patch will be rolled out.